XiaoMi Vacuum + Amazon Button = Dash Cleaning
by c0mmensal in Circuits > Assistive Tech
8632 Views, 23 Favorites, 0 Comments
XiaoMi Vacuum + Amazon Button = Dash Cleaning

This instruction will explain how to use your spare Amazon Dash Buttons to Control XiaoMi Vacuum.
I got a bunch of Amazon Buttons laying around from the times they were $1 and I had no use of them. But on the receiving of a new Robot Vacuum I decided that would be very convenient to use these buttons as a control to the vacuum.
Press Ziploc button and it'll vacuum the Bedroom.
Press Glad button and it'll vacuum the Living Room.
Press Fiji.. well you've got the idea.
It this project there are incorporated many hacks from the internet. I really appreciate the work so many people have done and think I have to share my little contraption based on their research.
Disclaimer: All step below you do at your own risk! If you follow the steps carefully there is very little chance you may damage something. But sh#t happens! And I take no responsibility of it. BTW all steps can be reversed so potentially there is no warranty violation. But of course - YMMV!
The basic principle is we catch the dash button press on the router and send webhook to Vacuum instead of buying stuff from Amazon.
What you will need:
- Router with custom firmware that can control DHCP, run scripts and fulfill get|post queries. Mikrotik, DD-WRT, OpenWRT, Tomato etc..
- XiaoMi Vacuum. v1 or v2
- Amazon Dash Buttons
Specifically what I used:
- Mikrotik
- XiaoMi v2 Vacuum Roborock S50
- Bunch of Amazon Dash Buttons
Here is the procedure:
- We root vacuum
- Install and configure necessary packages under root on vacuum
- Setup Amazon Dash button
- Setup Router to catch button request and control Vacuum
NB: In fact you don't have to root your vacuum to control it. If you have any other server on your lan (or wherever) who can run python or php you can direct webhooks to them. But I don't. And I wanted to keep it tidy and compact on the vacuum itself. So if you don't like my approach I assume you can figure out how to setup your own middle man server from this read. Just go straight to point 2.
Ok here we go...
Obtain the Token and Root Vacuum

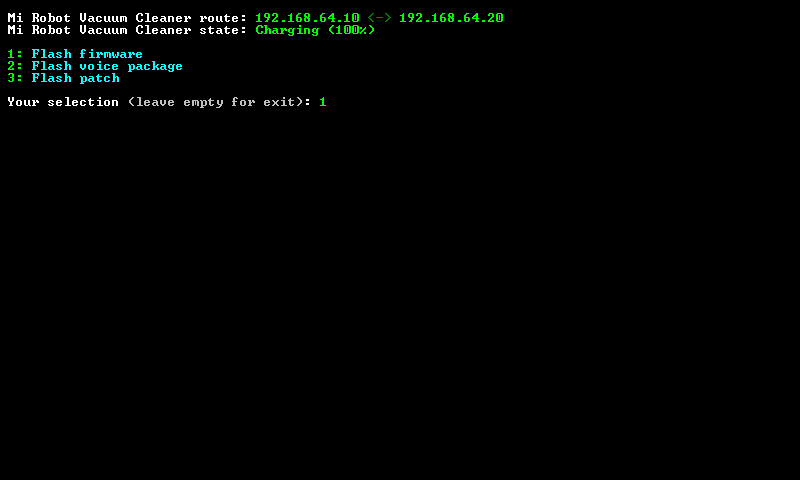
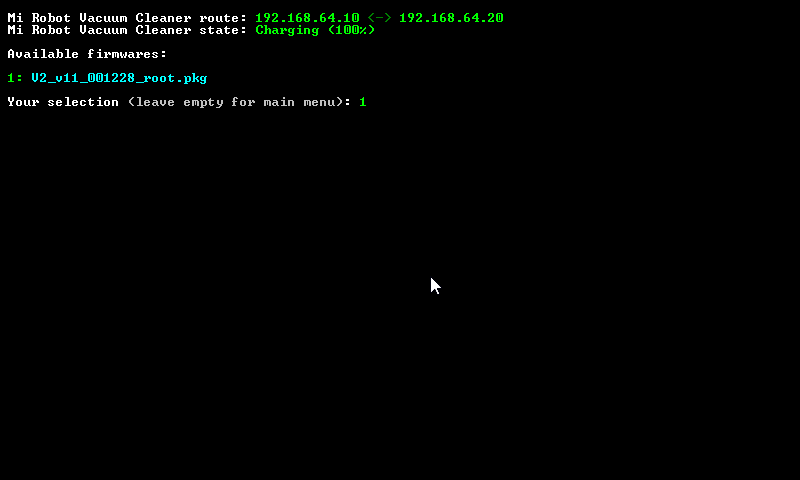
All software, fimware and instruction for rooting were obtained from:
http://4pda.ru/forum/index.php?showtopic=881982
If you have OS other than Windows and phone other than Android (you can use virtual with nox) please follow the link above (use Google Translate) and read the instructions otherwise follow with the manual here.
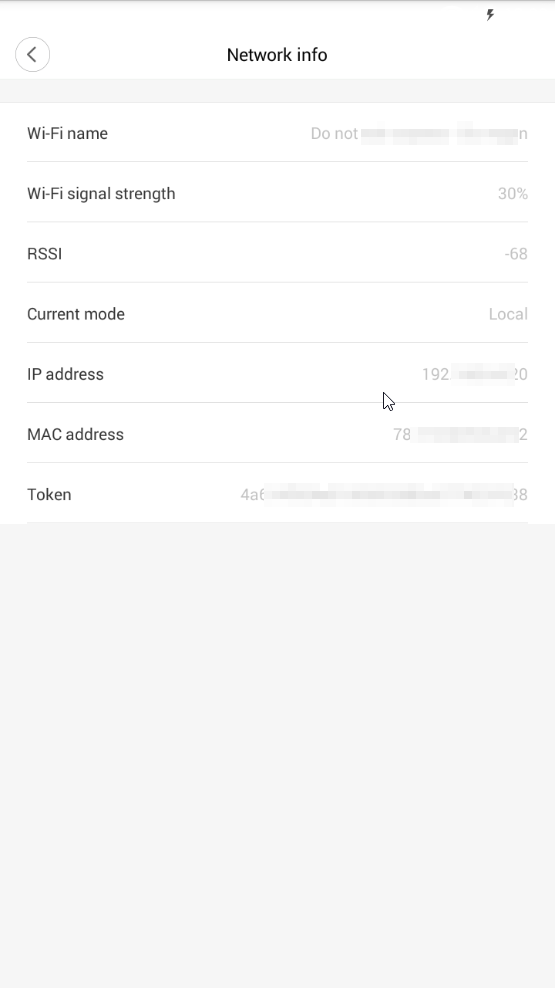
In order to root we need to obtain ip address and the token from your vacuum.
Unpack root.7z.
Please install Mihome from Vevs on your Android. You can use one from the Archive or if this instruction is dated then latest version can be obtained from his website (http://www.kapiba.ru/2017/11/mi-home.html) or his Google Drive (https://drive.google.com/drive/folders/1IyjvIWiGaeD7iLWWtBlb6jSEHTLg9XGj)
Login to your MiHome. You have to set China Mainland on your account and added Vacuum to it).
Tap on Vacuum icon --> Settings (Three dots on upper right) --> General Settings --> Network info
Fill in ip address and token in win-mirobo/win-mirobo.ini
Disable firewall in windows. Launch win-mirobo.bat and flash the firmware.
!!!!!!!!! V1 is for v1 Vacuum and V2 is for v2 Vacuum (Roborock S50)!!!!!!!
If you flashed wrong FW - go to 4pda link (first in this step) and read how to recover.
Arter Vacuum reboots - you have successfully rooted your vacuum and now you have access to it via ssh!
SSH to it (with Putty) with the cleaner/cleaner. Change to your password with passwd
Downloads
Install and Configure Necessary Packages Under Root on Vacuum
Premise:
Instead of webhooks MiVacuum uses miio protocol as does every XiaoMi IoT devices. So we have to learn it to understand webhooks. We need a middle man who can catch webhook and translate it to miio protocol to device. There is python library (https://github.com/rytilahti/python-miio) but we cannot use it on the vacuum since there is not enough space for Python 3.5+ on the Vacuum.
But thankfully there is a php-miio library (https://github.com/skysilver-lab/php-miio) which is comparatively very light and this is what we will be using (btw it is also used in win-mirobo above). The one who catches the webhook is webhook daemon (https://github.com/adnanh/webhook) who runs the script for php on incoming webhook.
SSH to your vacuum (with Putty):
#Do under root. Yeah I know it's not safe..whatevs.
sudo su #Here we install all necessities apt-get install -y wget php5-cli nano #Everything else is going to /opt cd /opt#Download php-miio #Check the latest on github. Correct lines below according to the latest wget https://github.com/skysilver-lab/php-miio/archive/v.0.2.6.tar.gz tar -xzvf v.0.2.6.tar.gz mv php-miio-v.0.2.6 php-miio rm -f v.0.2.6.tar.gz
#Download webhooks daemon #Check the latest on github. Correct line below according to the latest wget https://github.com/adnanh/webhook/releases/download/2.6.8/webhook-linux-arm.tar.gz tar -xzvf webhook-linux-arm.tar.gz mv webhook-linux-arm webhook rm -f webhook-linux-arm.tar.gz
#Create settings for webhook nano /opt/webhook/hooks.json #Input hooks.json content here. Right click in putty. #Ctr+X Save Y.
#Create script for calling php-miio nano /opt/webhook/mirobo.sh #Input mirobo.sh content here. Right click in putty. #Ctr+X Save Y. # Make executable chmod +x /opt/webhook/mirobo.sh
#Create autostart script and renew configs echo "/opt/webhook/webhook -hooks /opt/webhook/hooks.json" >> /etc/init.d/webhook.sh chmod ugo+x /etc/init.d/webhook.sh update-rc.d webhook.sh defaults
#Reboot the system reboot
After reboot test out your settings in the browser:
http://192.168.your.ip:9000/hooks/mirobo?method=find_me
method - command
params - parameters
All methods (commands) and parameters you can find here:
https://github.com/marcelrv/XiaomiRobotVacuumProtocol
Content of the hooks.json
Change your-token-here to your token from vacuum.
Correct ip-whitelist for your local network or remove completely if you run your hooks from elsewhere (unsafe).
[
{ "id": "mirobo", "execute-command": "/opt/webhook/mirobo.sh", "command-working-directory": "/opt/webhook", "response-message": "Executing mirobo script", "include-command-output-in-response":false, "pass-environment-to-command": [ { "source": "string", "envname": "token", "name": "your-token-here" } ], "pass-arguments-to-command": [ { "source": "url", "name": "method" }, { "source": "url", "name": "params" } ], "trigger-rule": { "match": { "type": "ip-whitelist", "ip-range": "192.168.1.0/24" } } } ]
mirobo.sh file content. Just copy-paste. There are only two lines (not 3).
#!/bin/bash
php /opt/php-miio/miio-cli.php --ip '127.0.0.1' --bindip '127.0.0.1' --token $token --sendcmd '{"id":'$RANDOM',"method":"'$1'","params":['$2']}'
Setup Amazon Dash Buttons
Open your Amazon App. Go to Dash Devices. Add new dash button as usual. On the promt to choose a product DO NOT. Close the app. You are done.
Setup Router to Catch Button Request and Control MiVacuum
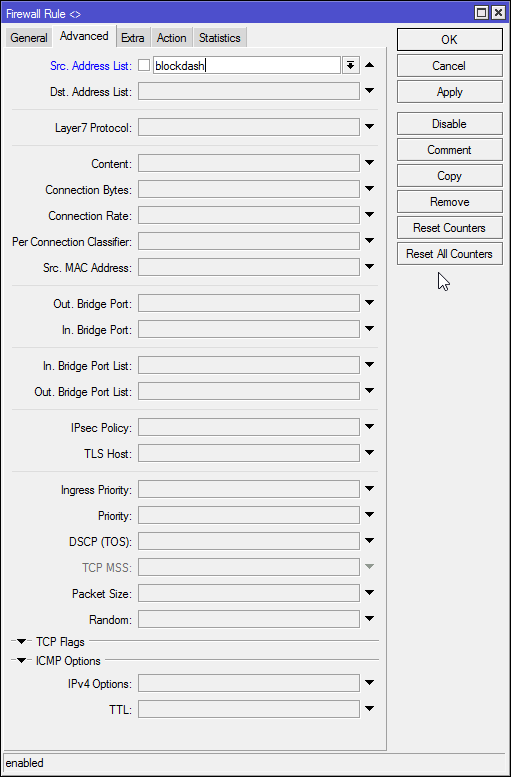
This works as follows.
When button is pressed it is associating with your network and asks dhcp server to assign an it address. We have to catch that request and perform a webhook to a vacuum. As an additional security measure we will block the connection to Amazon so that Amazon would not know we even pressed the button and has no ability to push firmware update or something else.
Mostly I use WinBox, but some times terminal is just easier.
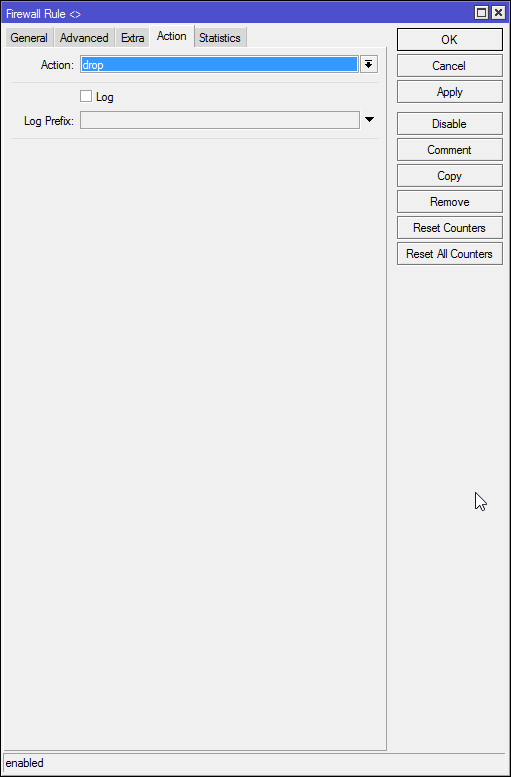
#Create firewall drop rule with address list to block /ip firewall filter add chain=forward src-address-list=blockdash action=drop comment="Drop Amazon Dash"
Then we have to create a dhcp lease rule for every button. Very easy to do in winbox.
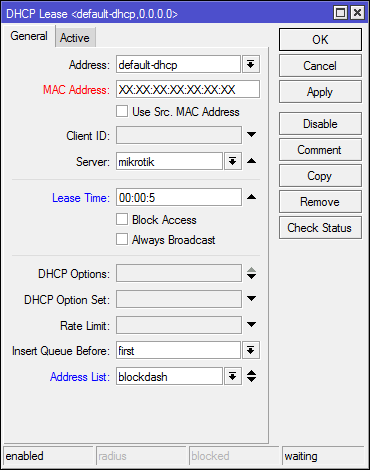
DHCP Server - Leases
Ones we press the button the new lease appears. We click it as static and set the address list to 'blockdash', set lease time to 5 secs (so that lease expires before the next press) and copy mac address for later.
#This command is just for reference if you added lease in winbox just skip it. /ip dhcp-server lease add address-list=blockdash mac-address=XXXXXXXXXX address=192.168.x.x lease-time=5s
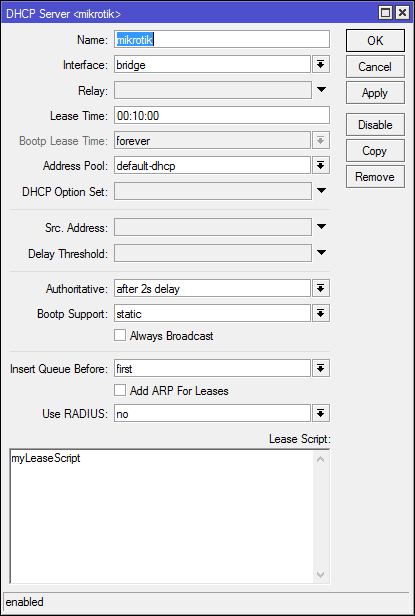
Now we have to point to lease script.
Open DHCP tab and add 'myLeaseScript' as a lease script on your dhcp server.
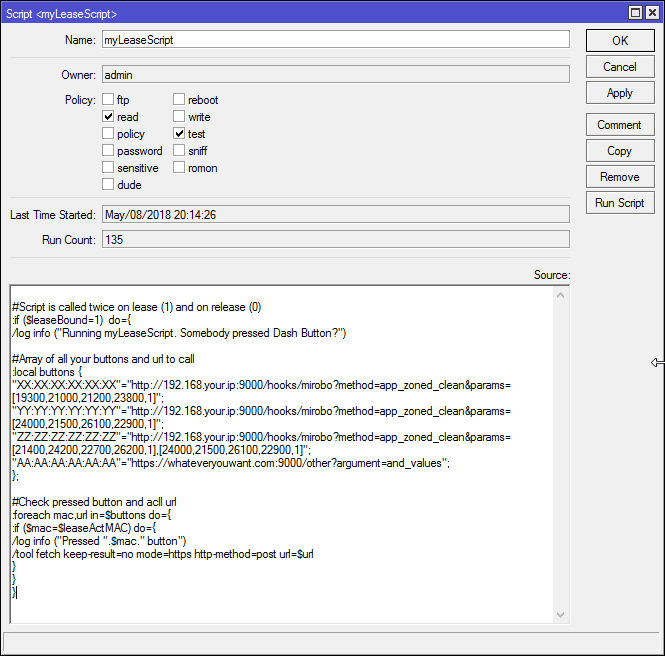
Now open System - Scripts and add 'myLeaseScript' with read,test permissions.
Content of myLeaseScript:
#Script is called twice on lease (1) and on release (0)
:if ($leaseBound=1) do={ /log info ("Running myLeaseScript. Somebody pressed Dash Button?")#Array of all your buttons and url to call :local buttons { "XX:XX:XX:XX:XX:XX"="http://192.168.your.ip:9000/hooks/mirobo?method=app_zoned_clean¶ms=[19300,21000,21200,23800,1]"; "YY:YY:YY:YY:YY:YY"="http://192.168.your.ip:9000/hooks/mirobo?method=app_zoned_clean¶ms=[24000,21500,26100,22900,1]"; "ZZ:ZZ:ZZ:ZZ:ZZ:ZZ"="http://192.168.your.ip:9000/hooks/mirobo?method=app_zoned_clean¶ms=[21400,24200,22700,26200,1],[24000,21500,26100,22900,1]"; "AA:AA:AA:AA:AA:AA"="https://whateveryouwant.com:9000/other?argument=and_values"; };
#Check pressed button and acll url :foreach mac,url in=$buttons do={ :if ($mac=$leaseActMAC) do={ /log info ("Pressed ".$mac." button") /tool fetch keep-result=no mode=https http-method=post url=$url } } }
Now you have automated your cleaning on a press of Amazon Dash Button. Have fun!
Please pay attention: It is very unsafe to send webhooks unencrypted. Webhook can use encryption, but however I tried to make it work it just never happened. Since I use it just in my local network I'm not too concerned. But if you wish to use it over internet to hook up to IFTTT with Google Assistant integration please pay attention to this fact! I'm not sure what was the reason for a crypto failure in my case. Self-signed certificates I beated with issued by letsencrypt. Overcomplicated network with bunch of NATs I beated with ipv6. But it seems to me webhooks works very bad with certificates and in fact very badly documented. And looks like IFTTT does not work with ipv6. I tried all I could, but failed. You might have a better luck. Don't forget to make a post.
upd: I have an idea how to make it more secure without encryption. You create a few scripts for every action you want to perform. You modify the mirobo.sh to call the script with for given parameter sent in webhook eg. clean_bedroom. That's it. The most person who exploit the hook will do is to clean your bedroom again and again... )) Once I do that I will update the instructable!
How to Plot Your Map
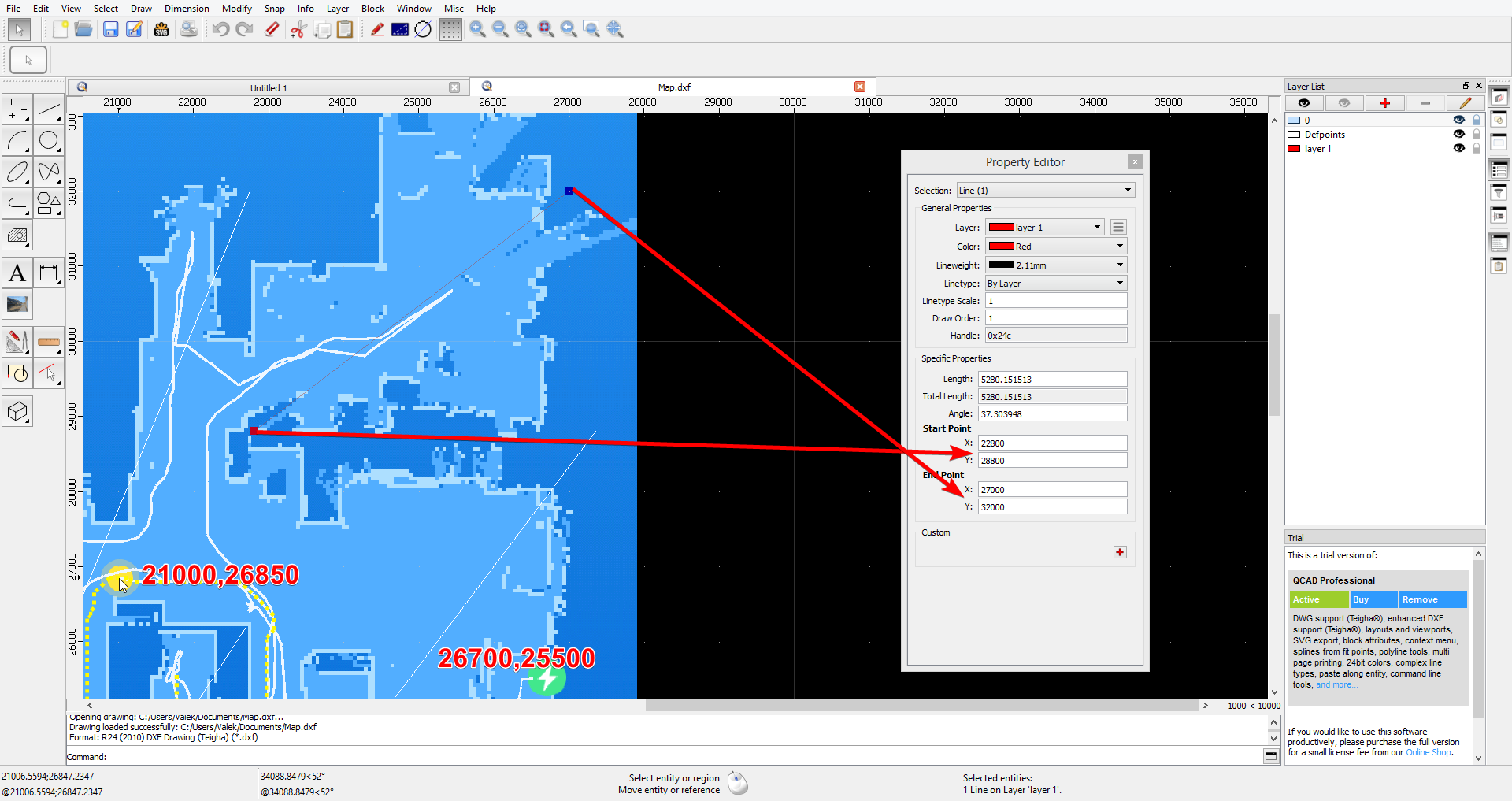
Once you have your full map ready in your MiHome app send your vacuum to a specific location via 'app_goto' command.
Make a screenshot of full map with position sent and base. The base point after reboot of vacuum is the position [25500,25500] THIS IS NOT THE POSITION OF CHARGING BASE, but if you reboot the vacuum at charging base then the position of charging base will be 25500,25500. So from known position sent and base position you can plot your map on any CAD program with the screenshot you've taken. I used free QCAD.
After fitting the image to the grid I use a line across the room to measure the start and end point of the zone.