Raspberry Pi Tor Relay

So obviously, TOR needs a large amount of servers and as TOR network is not a commercial organisation, it requires voluntary supporters. You can be one of them and turn your Raspberry in a TOR relay.
Parts Needed

- Raspberry Pi
- power supply
- network cable/connection to the Internet
- SDcard with Raspbian (you can find all necessary installation intructions here: http://www.raspbian.org/RaspbianInstaller)
Let's Start
Open a terminal
apt-get install sudo
adduser tor
passwd tor
this creates the user "tor" and let's you set a password. Please use at least 8 digits (numeric, alphanumeric and special characters)
Now we have to to add the tor user account to the list of sudoers:
nano /etc/sudoers
Add the line
tor ALL=(ALL) ALL
Now we'll install the latest security patchess and updates. Please do this regularly!!!
sudo apt-get update
sudo apt-get upgrade
Network Configuration
Now that the base setup is done, we have to configure network interface, open a terminal and use this command:
ifconfig
This shows you your actual configuration:
eth0 Link encap:Ethernet HWaddr 00:23:54:40:66:df
inet addr:192.168.0.20 Bcast:192.168.0.255 Mask:255.255.255.0
write down inet addr and mask
then type:
sudo nano /etc/network/interfaces
You will find a line like this:
iface eth0 inet dhcp
So as we see the Raspberry obtains an IP adress from the local DHCP server. If you want a static IP you hould change this to:
iface eth0 inet static
address 192.168.0.20 <- chose an IP that fits to your network! This is only an example!
netmask 255.255.255.0 <- change to the settings that fit to your network
gateway 192.168.0.1 <- type in the correct IP adress of your gateway.
Installation and Configuration of TOR

sudo apt-get install tor
If you're connected to the Internet a download will be started, this takes some time.....
Now we need to edit the TOR configuration file . You can find it here: /etc/tor/torrc. Open this file with your favourite text editor an add/change these settings:
SocksPort 0
Log notice file /var/log/tor/notices.log
RunAsDaemon 1
ORPort 9001
DirPort 9030
ExitPolicy reject *:*
Nickname xxx (you can chose whatever you like)
RelayBandwidthRate 100 KB # Throttle traffic to 100KB/s (800Kbps)
RelayBandwidthBurst 200 KB # But allow bursts up to 200KB/s (1600Kbps)
Problems With the Firewall

Start the TOR Server
sudo /etc/init.d/tor restart
TOR is now restarted. Now we have a look at the log file (less /var/log/tor/log). If everything is fine, you'll find an entry like
at the end.Oct 18 22:59:21.104 [notice] Tor has successfully opened a circuit. Looks like client functionality is working.
Congratulations! Now you have a TOR relay!
Configuring Your Browser to Use Tor
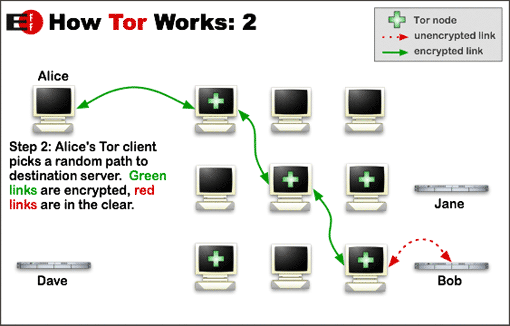
The first picture shows you how it works
An example: Let’s say you access instructables.com through Tor. Your Internet service provider and local network operator can’t see that you’re accessing this site – they just see encrypted Tor traffic. The Tor relays pass your traffic along until it eventually reaches an exit node. The exit node talks to instructables.com for you – from the perspective of this site, the exit node is accessing their website. (Of course, traffic can be monitored at the exit node if you’re accessing an unencrypted website.) The exit node passes the traffic back along the relays, and the relays don’t know where it ends up.
This makes it possible for Tor to offer anonymity and a path through Internet censorship and monitoring – people living under repressive regimes with censored Internet connections can use Tor to access the wider Internet without fear of reprisal. Whistleblowers can use Tor to leak information without their traffic being monitored and logged.
All this nice features have their price. Browsing with Tor makes it really slower. So you might now be able to see youtube videos, that are blocked in your country, but it may take some time until the video loads.
So how can you get this client and install it?
This depends on your operating system and browser. There are many good tutorials out there for almost every possible combination. You can find many other good (video) tutorials out there, but i think the following links should give you enough information for your first steps:
Windows: https://www.torproject.org/docs/tor-doc-windows.html.en
Linux/Unix/BSD: https://www.torproject.org/docs/tor-doc-unix.html.en
Debian/Ubuntu: https://www.torproject.org/docs/debian.html.en
Mac OSX: https://www.torproject.org/docs/tor-doc-osx.html.en
and last but not least:
Android: https://www.torproject.org/docs/android.html.en
Last words:
Remember not to provide any personal information – say, by logging into an account associated with you – while using the Tor browser, or you’ll lose the anonymity.