Encrypted Note Storage V2.0
by Northstrix in Circuits > Microcontrollers
818 Views, 2 Favorites, 0 Comments
Encrypted Note Storage V2.0
Encrypted Note Storage is a device that encrypts and securely stores your notes. It relies on the Serpent cipher for encryption and the HMAC built on the SHA256 hash function for message authentication. I did my best to make this device as affordable and easy to use as possible. You can also store the notes in the external database with an additional level of encryption.
Features:
- Integrity check;
- Message Authentication.
*UPDATED: Newer and better version of this device is available here https://www.instructables.com/Encrypted-Note-Storage-V30/
Supplies
You only need a single ESP32. Although in some cases, you might also need a 10mkf capacitor, only to flash the board.
Encryption Algorithm
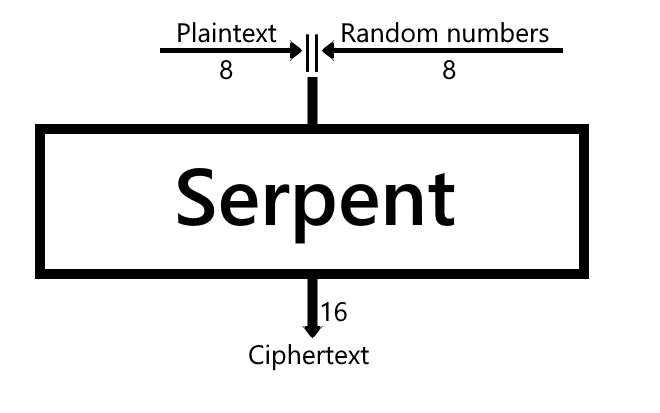
The encryption algorithm is as simple as it can be. I didn't depict the key on this diagram because its presence is obvious. MAC hashes the whole plaintext (it's not on the diagram too).
Output Structure
The first 64 characters of the output is a tag. Every 32 characters after that are the blocks encrypted with Serpent. If the plaintext length isn't multiple of eight, then the padding is applied.
Install CP210x Driver and Configure Arduino IDE *optional
If you've never flashed ESP32 before you'll need to configure Arduino IDE and install drivers to upload the firmware to the boards, you can download the CP210x driver here: https://www.silabs.com/developers/usb-to-uart-bridge-vcp-drivers
In case you don't have Arduino IDE, you can download it here: https://www.arduino.cc/en/software/
Configuring IDE isn't a part of this tutorial, you can read about it here: https://randomnerdtutorials.com/installing-the-esp32-board-in-arduino-ide-windows-instructions/
Download Firmware
You can download the firmware here: https://github.com/Northstrix/Encrypted_Note_Storage_V2.0
Download and Extract the Serpent Library
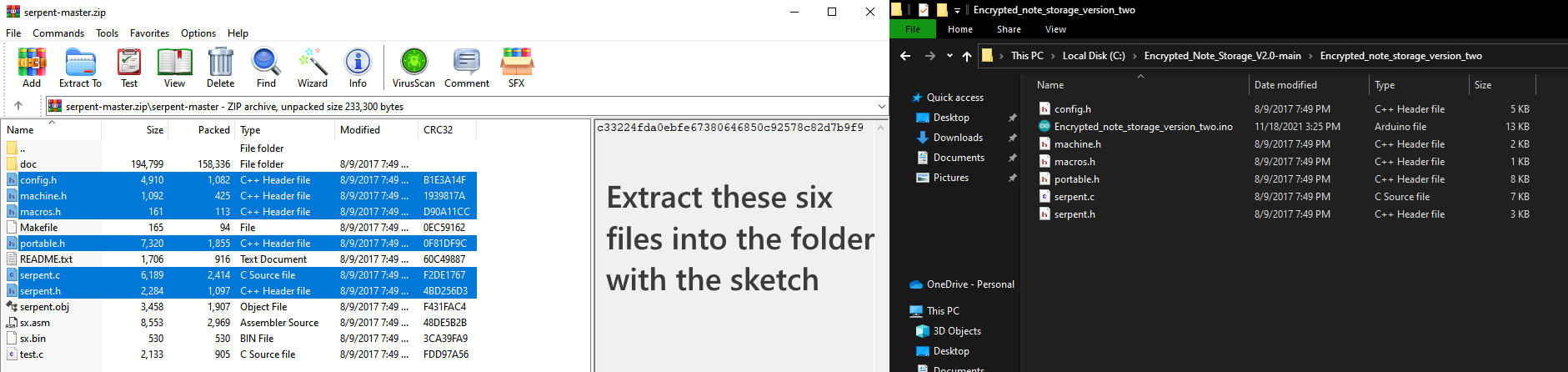
You need to download the Serpent library and extract it into the folder with the sketch.
Generate the Keys
The best way to do it is to throw 20-sided dice.
If you get a number from 1 to 9, write it down.
If you get a number from 10 to 15, write down a letter corresponding to that number.
10 = A;
11 = B;
12 = C;
13 = D;
14 = E;
15 = F.
If you get 20, write down 0.
If you get something else, don't write anything and throw the dice again.
If you don't want to use that method, you can use the random number generator from the same repository in GitHub. Just beware that it's untested. I can't guarantee that it produces a random output. Use it at your own risk. If you have a tested RNG, don't hesitate to use it instead!
The serpent key must be exactly 64 characters long.
MAC's key can have an arbitrary length. I would recommend you to make it longer than 300 characters. In my case, it's 329 characters long.
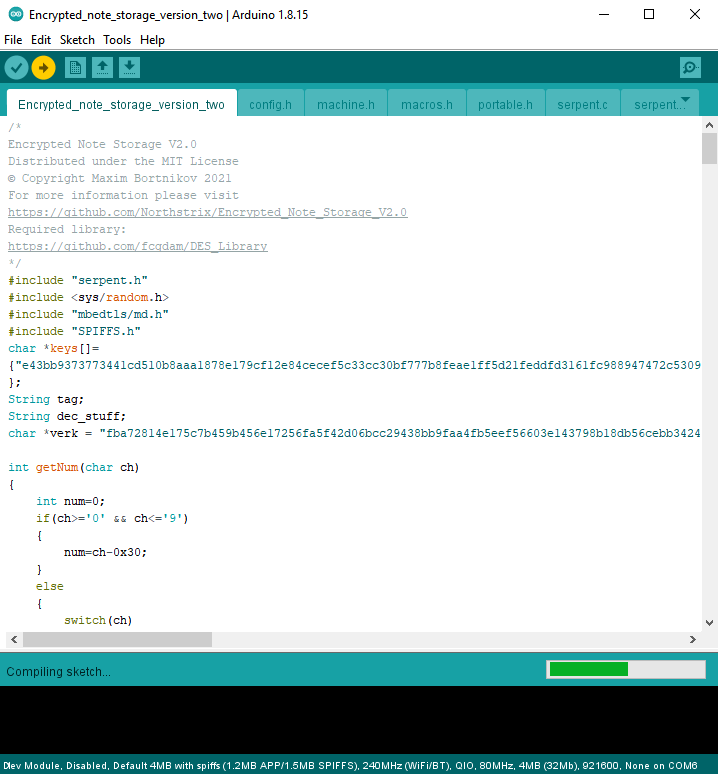
Modify Firmware
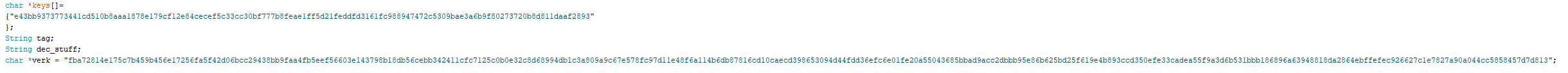
Open the file Encrypted_note_storage_version_two.ino and replace the existing keys with those you've generated.
Flash ESP32
Some boards will flash without any problems.
Unfortunately, that's not the case for all boards. if you configured IDE correctly, installed drivers, and selected the right port, and still keep getting this error: A fatal error occurred: Failed to connect to ESP32: Timed out waiting for packet header
Connect a 10mkf capacitor to the board while flashing.
Connect the positive lead of the capacitor to the EN pin of the ESP32
Connect the negative lead of the capacitor (usually indicated by the gray stripe) to the GND pin of the ESP32
Encrypt Record
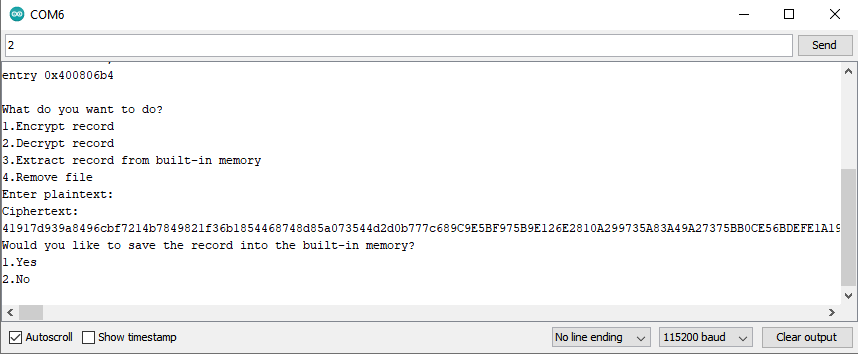
I was able to encrypt and then decrypt a 1000-characters long plaintext without any problems whatsoever!
You can encrypt a 5000-character plaintext without any problem. But you won't be able to decrypt without breaking it into four parts, and in that case, the integrity check and message authentication won't work!
Important note: The feature of saving ciphertext into the built-in memory is untested, and there's no guarantee that it will work correctly. Work with the built-in memory at your own risk.
To encrypt a record:
1) Open the Serial Monitor;
2) Set the baud rate to 115200;
3) Reboot the board
4) Enter 1 into the text field, and press send;
5) Enter the plaintext into the text field, and press send;
6) Copy the Ciphertext from the text box.
7*) If you want to save the record into the device's built-in memory, enter 1 into the text field, press send. Enter the filename and press send, after that, paste the ciphertext into the text field and press send again.
As you might've already guessed, storing the tag in an unencrypted form makes this device vulnerable to the chosen-plaintext attack. Beware of it!
Eventually, I came up with these results.
Plaintext:
Encrypted Note Storage is a device that encrypts and securely stores your notes. It relies on the Serpent cipher for encryption and the HMAC built on the SHA256 hash function for message authentication. I did my best to make this device as affordable and easy to use as possible. You can also store the notes in the external database with an additional level of encryption.
Even though the main feature of this device is message authentication, it also comes with a cryptographically strong encryption algorithm. The biggest known flaw of this device is that an attacker can discover the content of the message by implementing a chosen-plaintext attack, but I wouldn't be worrying about it too much because an attacker needs either the device or the keys that you've generated for your device to discover the content of the message by using this attack. Even with the HMAC's key, the brute force is infeasible unless your note is just several letters long.
Serpent key:
e43bb9373773441cd510b8aaa1878e179cf12e84cecef5c33cc30bf777b8feae1ff5d21feddfd3161fc988947472c5309bae3a6b9f80273720b8d811daaf2893
HMAC key:
fba72814e175c7b459b456e17256fa5f42d06bcc29438bb9faa4fb5eef56603e143798b18db56cebb342411cfc7125c0b0e32c8d68994db1c3a809a9c67e578fc97d11e48f6a114b6db87816cd10caecd398653094d44fdd36efc6e01fe20a55043685bbad9acc2dbbb95e86b625bd25f619e4b893ccd350efe33cadea55f9a3d6b531bbb186896a63948818da2864ebffefec926627c1e7827a90a044cc5858457d7d813
Ciphertext:
41917d939a8496cbf7214b7849821f36b1854468748d85a073544d2d0b777c689C9E5BF975B9E126E2810A299735A83A49A27375BB0CE56BDEFE1A19B91EC6C839B18D3F501F6BF163FAB1BF5AFE8337F307360F13CF77B862499FA227037C5ED8D4D2DC345C087B39D7EF917EDD219CA803BA45E3E7CE52A8749A334535EB37660EC6A0034EA9E8B8DF5B3CC6AF795529D62D9389076231661E6D43839E94F46941B5F850816F15CF7CF5068105F5407B3DD319A766E673EA0F7A3AF5763E881871765F0EF9DC6DFDDA54E1D59C50187A3C17D4A7A5D02BFCF70B5436FB207F1A3CAF073D7FDB91CE3804124F745AF68F6BDC72D2580B0613B364CDA78AEE71AF9C9BB3BA1F1B38E59C2C39646D4C77BC4DBD786FBE8AADB39A8AA0275DCCB1C750122402845052D6053AA7A3B42402216CB1EB1C9AF2A373FE3E313AE6AB1C504E16962907D94D759DC2E9C7E8756506809A265F37DFBB9FFE1112AF574F8959E04646D0DAC836BCF8603D6F3158F54C0710AB918533F7E5F46087D21EAD40D9E6D2E262B4FEEE7ABC2EEE961DF0CFF35D6709F38CB7C9DE89B4D4B2E1F9B7F371A16EF67EDB865016585DA1C69AEBD7A7671597DF402AA99690ADC05B743FC21F1B4659EE1C5E9BB9805DF2D99A89B3CA734BCA58179171D1819BA26921DFFB8664AF1D683496911C544A6CECFBE2619B2BC6AA4F036A667AD8A23A55AE28DE8786DA68A61E58E94321E6723E508BD94B185C76D71D90A4CC979302285B68DDF502CEA1906251A8CE04FDC5389DFC7647D8541364CBBD787C5C171119DF49993E7B8384F6A11E70CBA07C2FAEA460D55500E84F26CAE21C428605DB465E66FE2F2914913F955AA1F95C3B6D7BE866AC8BCB0DFB33D65836947DC8BBB87B8908F1B4910FA98B8E17942051264FA4D870B93D0320123E6A49FA339025D3AE7D9B93C449A98822846777713B8A0E896D4C9C6A23BCDA2C0D71F2697C5C0483C83E62A48CD479B4002F70A3BF75B340328C22B1C05BFB86F13CF59C2F08583E65FC54FE6A5AB1E62503DEDDEE2131E2BF0DE5E61545C4A465D401D3A3183F04316B254FD549913EEA657965BAB159B848E8416A4FF2572D74282A1F65247DF2B33308D1B258143F72AF593A9DE4E3B2F0C219C03CB6FE9A4FE96E7D1944D7972A4D9E925089B2A7C6816615C5156E6688A1A2C312A5F028CBF554EF72CF25A08CBA9C2E5554EC074671D903E1628CFF888BC0BC8D9B0250F4CE8E57D1C471A3DEFB207843CA10DE4B090D87B1091CE1A5BF717790E9537C2DEABF76817C9958D5691632A4A843A063F9122D6AB18F12C729A24761A241673FC8397CA18925602C0F7B52C4C1F875E3B53492250E4EA9F70482D204D524A76C0461D7FF083A48226F08804134CD8C44C5B4AEA877D8D59AECD9386B1541004B859F28F345E39485918613C18B0598A5E01D0680884E53F278E9C7B5EAD27A90FF21C4005B1BC4DBC2C61181E56950913ED2AD2118AE7FD25D2191E016CAA3CB7CEFA37929CCA19BFDECE53DAFA109815711A36E6E7D7134DAA6AC4BBF611709BD62B08C0850D7160C1EF8504B12A34702D2F3FE11C13CD1AFBB2A49148F12C4C772068ED41EF68C342B36F07AC6DDD775BE6965C5F88DFD867E15E16642B0B7F562E2566E89241435E5AC4F526C250F78AEB8E59714713677FA9E1CF616AD50BA8A6A92317D20975380EFFF06630F59D94E68E33FBCA221E1B52B2B3CE11F456D84E0FCEE4FDD6C84E8C814970A1996EC092A47ADF1AC56EEC523BDFA1BBA23B03E8D67CD91824ED60E07B30225785FB159C1E64E9B69C63A5564C66B9B4EFCE49379030B65ABBDD77A9C246175B2A15E5E59833CD34949E31D41DF05878046B4C749F50724D450F0B83A220582FD426AE342B880CDE4D04EFF73F523B98A0B46F897CCB4A6565E2BB4423ED032B34B44DAE4B33F6705095ED9E0243178B32B02D75372B1B9E8D1929F4D3046BE8F13872652808765485B51CDF956A0F20C3C7597FFD3D461B715DC5099131AEBD72FD957F49364E0E842C35D838E3C7DDD16E348B12000C7B2EEB1C8CF4B823D0659C20173B782D98CE895AEEBA6C23972C811896BEF50E5B0A9B0D07A7C6F70BDB59541E1586BF8428096300F07D72331118F8AEA33690921828C5F8B8860F89F556D13EBBB6C18D5C6341BF76477DEEE3DAB1652419E41C4E5CF629957375771AA3C05D33201EDD3A2872B703865C10219A64EA9FE949EE873FB0607591B54BD45AEC3EDA9451CB1E392F96DA6A4639F15B642BEC8897B752705E07E46FD907271BA14546E2631DAA890C07B9A25953749CE50912687E6A90310193217802763A2AE1526BD87702447A51215E408B5C6BC3733FDAB7ECD5F4FA377058D2207151F2A51514A4551AB3BE3A5A546C5B3EA274CD64BFB433570BF60DA679F7A51ECF3920D045A45903FF3CCEDC4C8A0F6B9046F132652DBD668FB108AFC097DF3A01AB837618EFF694239B74B7025FABEFAD03C7BAD20856E1D8132A01ACCE80A33E56146301DE79CEF287930573BFFEA7C61691B95D7EB5E68B2ADCABFA06E959FB1BFF2F24864A52860B0C950716BD7CCB76B33C42DA7D6D47C5D5B105A6E4DD4D6DEA04CB38D4E6BB2BC9B2C1569DD8196EC5AD06B5012EFAC02E2C304ABF31F97A9C738A41315920363467D2C17B7995FFF6969381C07DCE778EF6B3C12B786E5254C14C7D30015A698D2047CCF2252DADDA1CFD785F78730
Decrypt Record
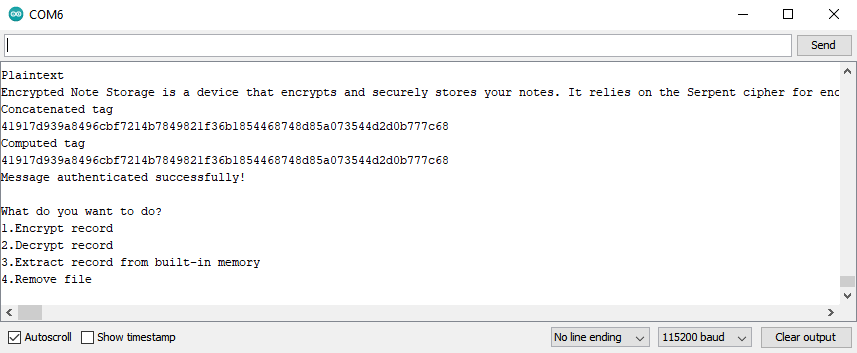
To decrypt a record:
1) Open the Serial Monitor;
2) Set the baud rate to 115200;
3) Enter 2 into the text field, and press send;
4) Enter the ciphertext into the text field, and press send.
The device decrypts the note and then computes the tag for it. If the tag attached to the ciphertext is the same as the computed tag, you'll see a message: Message authenticated successfully!
Otherwise, you'll see: Failed to authenticate the source of the message!
Extract Record From Built-in Memory *experimental
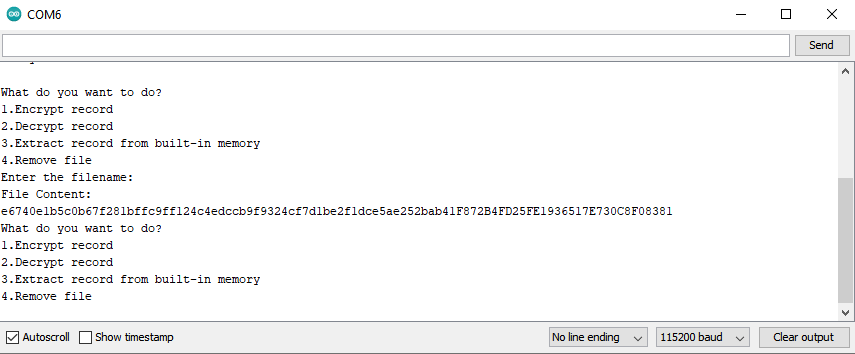
Records stored in files.
Let's suppose that there's a file in memory with the name Note and the content e6740e1b5c0b67f281bffc9ff124c4edccb9f9324cf7d1be2f1dce5ae252bab41F872B4FD25FE1936517E730C8F08381
To extract the content of this record:
1) Open the Serial Monitor;
2) Set the baud rate to 115200;
3) Enter 3 into the text field, and press send;
4) Enter the filename into the text field, and press send;
5) Copy the content of a record.
Remove Record From the Built-in Memory *Experimental
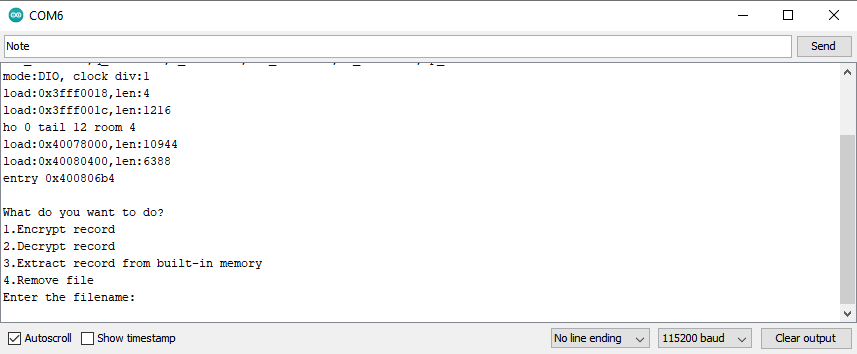
To remove the file:
1) Open the Serial Monitor;
2) Set the baud rate to 115200;
3) Enter 4 into the text field, and press send;
4) Enter the filename into the text field, and press send.
Add a Record to the Database
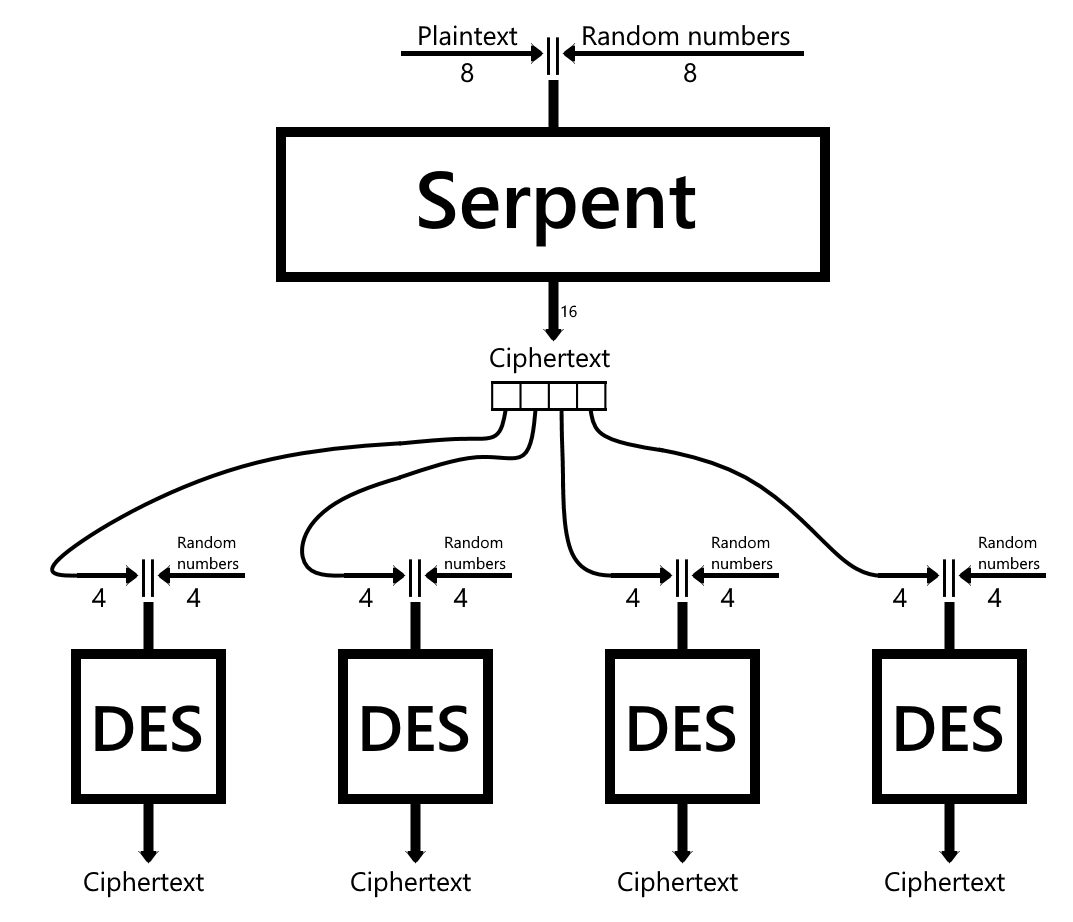
Built-in storage is limited and still untested. There are much better and more reliable options to store your notes. I can only suggest one of my previous projects called Twinkle. Twinkle encrypts all records with DES. It adds another level of encryption and kinda solves the problem of the chosen-plaintext attack (but only if the ciphertext obtained by an attacker is a ciphertext from Twinkle or another encoder that supports randomized encryption).
The extended encryption algorithm will look like this if you store the encrypted notes in Twinkle.
Generate 16 Character Key
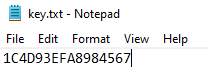
Twinkle requires a 16 character key to encrypt and decrypt your notes.
And again, throw the dice.
Since I'm going to expose the key to the whole world, I've reused a key from a previous project, don't ever do that! Always generate your own keys, and never reuse them!
Load Key Into the Twinkle
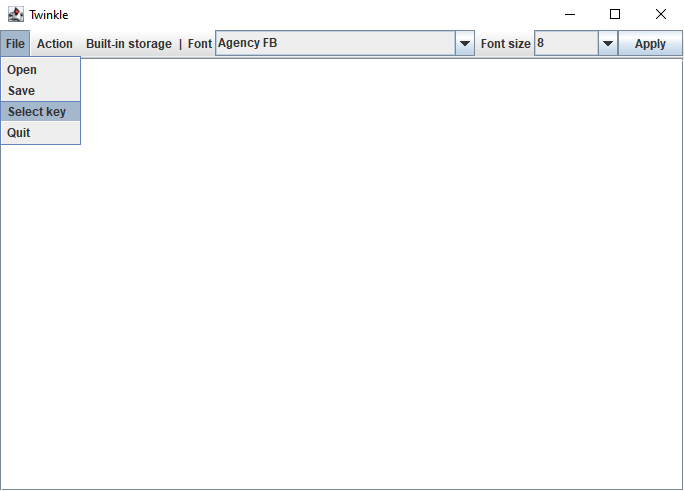
To load the key, click File -> Select key. In the pop-up window, locate the key that you've generated, click on it, and then press Open.
You need to load the key every time you're opening the program.
Save Record
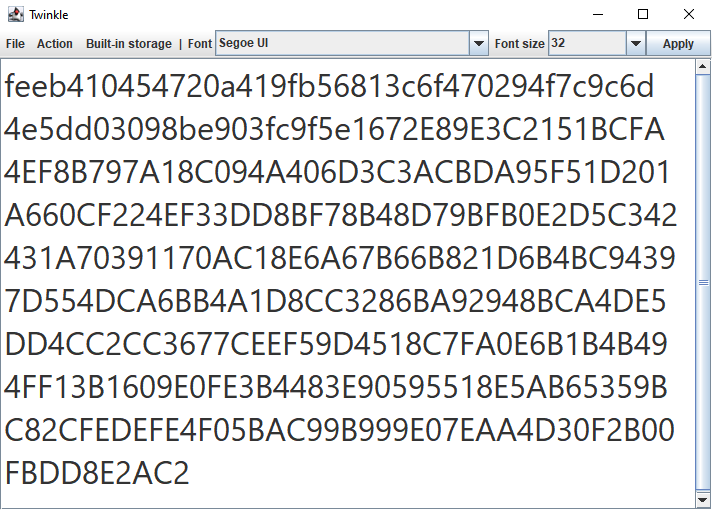
To save a record: Paste the encrypted note into the Twinkle, and then click File -> Save. After that, navigate to the folder where you want to save your record, enter the name of the record, and press Save.
I've chosen the name Note.txt
Create Table
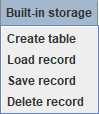
To use a built-in database you need to create a table for the data (Built-in storage -> Create table), You only need to press this button in two cases:
1) You've never pressed it before;
2) You've deleted the file called stuff.db
In case of successful creation of the table, you will see the corresponding message.
If you press this button without a need to do so, you will get a pop-up window with the error.
Add Record to the Database
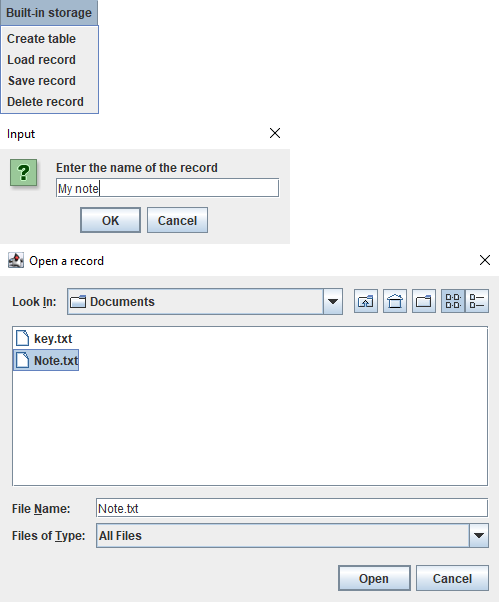
To add a record to the database, click Built-in storage -> Save record. Name your record as you wish and press OK. Now, navigate to the record that you've saved in step 16, select it, and press Open.
In case of success, you will get a corresponding message.
Extract Record From the Database

Let's suppose that a couple of days have passed, and now you need to retrieve your note from the database and decrypt it.
To retrieve the record from the database, open Twinkle, load the same key that you used to encrypt the record, click Built-in storage -> Load record.
In the pop-up window select the record that you want to load and press Select.
Copy the encrypted note from the text box and decrypt it the same way you would decrypt any other note (step 10).
Final Thoughts
Even though the main feature of this device is message authentication, it also comes with a cryptographically strong encryption algorithm. The biggest known flaw of this device is that an attacker can discover the content of the message by implementing a chosen-plaintext attack, but I wouldn't be worrying about it too much because an attacker needs either the device or the keys that you've generated for your device to discover the content of the message by using this attack. Even with the HMAC's key, the brute force is infeasible unless your note is just several letters long.